The components of the NPS to configure are: System Health Validators, Health Policies, Network Policies, Connection Request Policies, RADIUS Clients and Servers and Remediation Server Groups, as indicated in the screen shot.
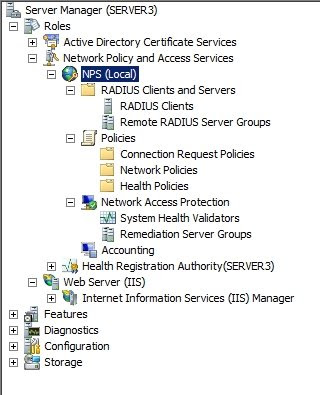
To configure these components I'm just going to take the easy way and use the configuration wizard.
Step 1: NAP wizard: launch the wizard by clicking on Configure NAP in the details pane of the NPS.

Now in the wizard, choose the following uptions:
a) select IPsec with Health Registration Authority (HRA) and give it a name
b) no Radius clients are being added, since the HRA is installed on the NAP Health Policy Server
c) we are going to apply to policy to all users, so we don't need to add any machine groups
d) make sure the Windows Security Health Validator and Enable auto-remediation of client computers are selected
e) Finish the wizard
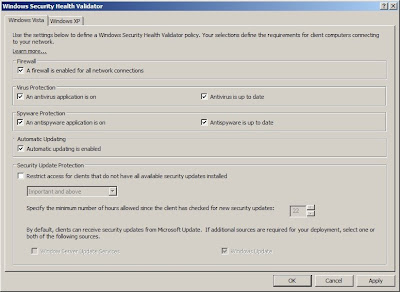
Step 2: Configure the SHV (System Health Validators): By default, the WSHV is configured to require firewall, virus protection, spyware protection, and automatic updating. You can easily change this in the Properties of the SHV.
Step 3: Configure a GPO for the NAP client settings: now we can start enforcing specific client computers to apply to our NAP. To do this, create a new GPO and define the following settings:
a) Computer Configuration/Policies/Windows Settings/Security Settings/System Services/Network Access Protection Agent --> Define the policy: Automatic
b) Computer Configuration/Policies/Windows Settings/Security Settings/Network Access Protection/NAP Client Configuration/Enforcement Clients --> Enable IPsec Relying Party
c) Computer Configuration/Policies/Windows Settings/Security Settings/Network Access Protection/NAP Client Configuration/Health Registration Settings/Trusted Server Groups --> New "Trusted HRA Servers" --> Add URL "Https://NPS.Test.local/domainhra/hcsrvext.dll" --> Finish
d) Computer Configuration/Policies/Windows Settings/Security Settings/Network Access Protection/NAP Client Configuration --> right click and choose Apply
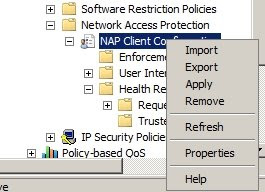
e) Computer Configuration\Policies\Administrative Templates\Windows Components\Security Center --> Enable Turn on Security Center (Domain PCs only)
f) close the GPO editor
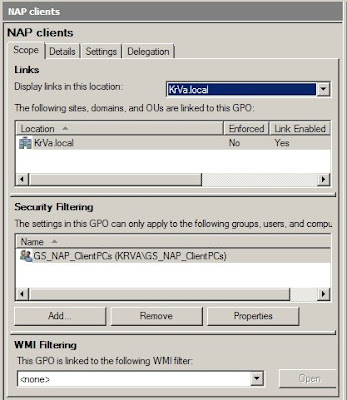
g) go to the Security Filtering of the GPO and Remove the Authenticated Users and Add the security group created earlier. In my case, that would be GS_NAP_ClientPCs.
And there you have it, IPsec NAP is installed, configured and ready to be used. In my last post about IPsec NAP I'll be using a Vista client to try and connect to the secure network section as an example.
Network Address Protection (NAP) posts:
IPsec NAP: Network Address Protection in Server 2008
Configuring IPsec NAP (Network Address Protection) - Part 1: Certificates
Configuring IPsec NAP (Network Address Protection) - Part 2: Installation of the NPS (Network Policy Server)
Configuring IPsec NAP (Network Address Protection) - Part 4: Testing with a NAP client


1 comment:
Your blog is very nice
Post a Comment