But before we start, let we tell you my setup:
Account Domain:
Server2
AD DS - FS
192.168.46.1 /24
DNS: 192.168.46.1
krva.local
Resource Domain:
Server3
AD DS - FS - Webserver
192.168.51.1 /24
DNS: 192.168.51.1
test.local
Client PC:
XP
client in krva.local
192.168.46.101 /24
DNS: 192.168.46.1 / 192.168.51.1 (IMPORTANT)
Global Security Group: FedServ_GS
User Account: KrVa
created in krva.local

Of course, in a production environment, it's not quite the idea to install FS on your DC's, nor is installing the IIS on a DC ...
As for the rest, no trusts have been configured between the domains.
While you are installing your environment, a little bit more information about Federation Services:
1. AD FS provides a SSO (Single Sign On). It is an identity access solution that provides browser-based clients (internal or external to your network) with seamless, "one prompt" access to one or more protected Internet-facing applications, even when the user accounts and applications are located in completely different networks or organizations.
2. AD FS makes secondary accounts and their credentials unnecessary by providing trust relationships that you can use to project a user's digital identity and access rights to trusted partners.
3. AD FS makes a clear distinction between the Resource organization and the Account organization. The Resource organization owns and manages the resources that are accessible via the internet. The Account organization owns and manages the user accounts that FS links to security tokens that are used to authorize the users in the Resource organization.
OK, now that we have a basic understanding of Federation Services and you know my test setup. Let's do this thing.
STEP 1: FS - Installing the Federation Services (in both domains)
1. To do so, open the server manager and install the Active Directory Federation Services server role. If IIS is not yet installed on your server, it will automatically be installed.

2. You will need a certificate for SSL encryption. If you have a Certificate Authority (CA) you can use it to create a certficate. If not, choose to create a self-signed certificate during the FS installation. Of course, if you do this in a production setup, that is not the best option ...

3. For the token-signing (that's the security passport a user gets at login that is used to authenticate them in the "Resource domain"), we also create a self-signed token-signing certificate.
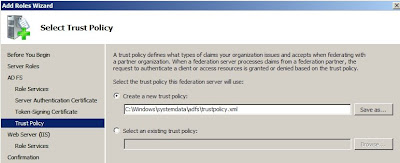
4. Lastly, we need to choose our trust policy. Since we don't have a trust policy yet, we will create a new one. So choose the path to which to safe you xml file (default option is C:\Windows\SystemData\adfs\trustpolicy.xml and there really isn't a reason to change that) so accept it and continue to the install section.
Next, we'll be configuring IIS to use SSL on both Federation Services Servers. Next out the next post.
Federation Services setup posts:
2. Setting up Federation Services (FS) in a Windows 2008 (WS08) environment: Part 2: Configure IIS to use SSL on the FS servers
3. Setting up Federation Services (FS) in a Windows 2008 (WS08) environment: Part 3: Configure the FS certificates
4. Setting up Federation Services (FS) in a Windows 2008 (WS08) environment: Part 4: Configuring the FS server in the Account domain
5. Setting up Federation Services (FS) in a Windows 2008 (WS08) environment: Part 5: Configuring the FS server in the Resource domain
6. Setting up Federation Services (FS) in a Windows 2008 (WS08) environment: Part 6: Creating the federation trust on both sides


No comments:
Post a Comment